Information technology (IT) is no longer a tucked away department with little impact on day-to-day affairs. It’s big business that’s involved in almost every sector of the economy, and therefore carries some major risks. Read on to learn the importance of IT risk management.
Unique Challenges of IT
IT (information technology) has become so integrated into our personal and professional lives that it touches upon almost everything we do. Due to its expansive influence, it’s essential to talk about risk management in IT.
IT project management offers unique scenarios, and therefore, unique risks. For example, can the hardware, software, apps and integrations keep up with ever-changing technology? A setback, limitation, risk, error or threat in IT can impact every facet of a business. To mitigate negative outcomes, it’s worth investigating an IT project management software that can help you manage risks in IT and other projects.
Then there’s the problem of finding the right people to address IT risk management, those with training and expertise in the space. These people, ideally led by an IT project manager, will also need to have a good work ethic, so that they’re dependable and will commit to their responsibilities.
But there’s another piece of this puzzle to consider before moving on with the discussion: complying with regulations, which are changing and updated often.
Steps to IT Risk Management
IT risk management is the application of risk management methods to information technology to manage the risks inherent in that space. To do that means assessing the business risks associated with the use, ownership, operation and adoption of IT in an organization. Follow these steps to manage risk with confidence.
1. Identify the Risk
You can’t prepare for risk without first figuring out, to the best of your ability, where and when it might arise. Therefore, both manager and team must be alert to uncovering and recognizing any risks, then detailing them by explaining how they might impact the project and outcomes. One method is using an IT risk assessment template.
2. Analyze the Risk
Once you’ve identified risk, you then must analyze it and discern if it’s big, small or minimal in its impact. Also, what would be the impact for each of the risks. Study the risk and how it might influence the project in various ways. You’ll add these findings to your risk assessment.
3. Evaluate and Rank the Risk
Once you evaluate the impact of risks and prioritize them, you can begin to develop strategies to control them. This is done by understanding what the risk can do to the project, which is determining the likelihood of it occurring and the magnitude of its impact. Then you can say that the risk must be addressed or can be ignored without faulting the overall project. Again, these rankings would be added to your risk assessment.
4. Respond to the Risk
After all this, if the risk becomes an actual issue, then you’re no longer in the theoretical realm. It’s time for action. This is what’s called risk response planning in which you take your high-priority risks and decide how to treat them or modify them, so they place as lower priority. Risk mitigation strategies apply here, as well as preventive and contingency plans. Add these approaches to your risk assessment.
5. Monitor & Review the Risk
Once you act, you must track and review the progress on mitigating the risk. Use your risk assessment to track and monitor how your team is dealing with the risk to make sure that nothing is left out or forgotten.
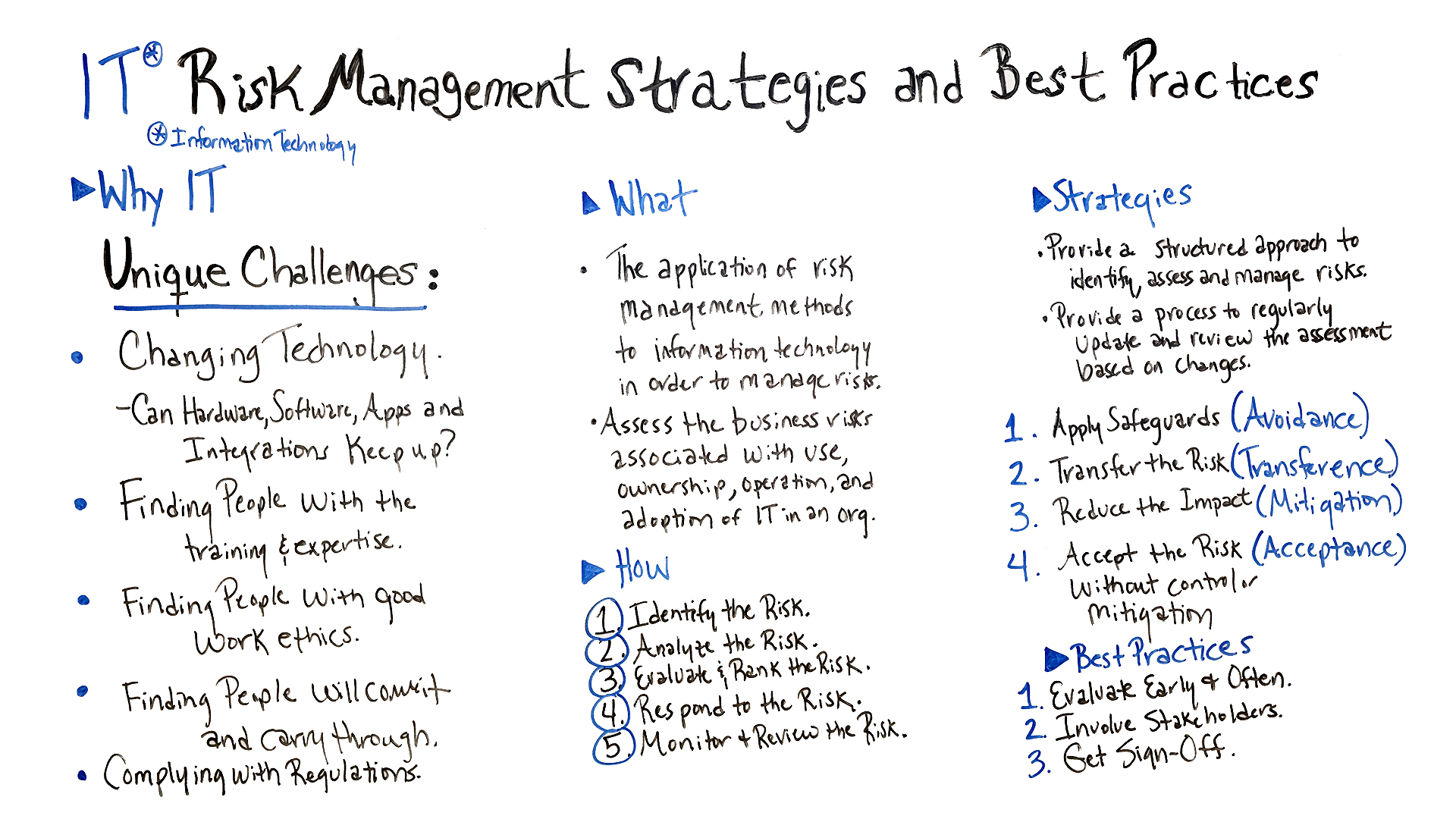
IT Risk Management Strategies
Strategies are a way to provide a structured approach to identify, access and manage risks. They provide a process to regularly update and review the assessment based on changes.
Apply Safeguards
This is an avoidance strategy, where the company decides to avoid risk at all costs and focuses a great deal of resources to that end. If you can avoid the risk, then it is no longer a threat to the project. However, there is a downside to this. If you avoid the risk, you also avoid the associated potential of its return and opportunity. So, it’s a decision not to take lightly.
Transfer the Risk
This is a transference strategy, when the company transfers the risk to another entity. This redistribution can be onto the company members, some outsource entity or an insurance policy.
Reduce the Impact
This is a mitigation strategy, where the company works to reduce the impact of the risk through methodology, teams or whatever resources are at its disposal. It can involve small changes, but always must come by process and a plan.
Accept the Risk
This is an acceptance strategy, where you know there is risk and accept that, so when and if it occurs you can deal with it then and there. This is sometimes unavoidable, but manageable if you have followed the steps in your project risk assessment template.
Best Practices for IT Risk Management
Here are six best practices when managing risk in IT.
- Evaluate Early & Often: There’s no better time to start on the risk management process than now, so begin early. Remember it is a process and so it will continue throughout the project. Then continue monitoring all the time. Risk never sleeps.
- Lead from the Top: Good leadership is many things. One aspect is developing a risk culture at the organization. That means valuing input from everyone, believing in the importance of acknowledging risk and keeping a positive attitude about responding.
- Communications: Having a clear channel to communicate risk throughout the organization is paramount to identifying and responding quickly and effectively to risk.
- Strong Policies: If there is not already a process and plan to deal with risk, you’re always going to be one step behind. This is again why a project risk assessment is key, but so is understanding roles and responsibilities for everyone on the project team, having a continuity plan, etc.
- Involve Stakeholders: A great resource that is often overlooked are the project stakeholders, who have a unique perspective and can provide insight into areas where risk might arise. So, involve them throughout the process, from asking for their participation with the risk assessment template and over the whole course of the project.
- Get Signoffs: At every stage of your risk management, get people to sign-off on the strategy, which includes the stakeholders.
Pro-Tip: Collecting risk, assigning ownership of those risks and then tracking them is crucial to any IT risk management strategy. There are software programs that can handle this, but if you want to take baby steps, a risk register template helps keep track of all those balls in the air.
ProjectManager.com and Risk Management
ProjectManager.com is a cloud-based project management software, which means that the data inputted is immediately updated, giving you the most accurate gauge to measure your project’s progress and catch any issues before they become risks.
Your risk assessment template can be uploaded into our online Gantt chart, where team members can receive assignments, comment and collect related documents, all of which can be attached to the risk.
The real-time dashboard tracks your progress across a number of project metrics. And reports can be filtered to show the information you want and then generated with one-click to present to stakeholders. Try ProjectManager.com today with this free 30-day trial.
Training Video on IT Risk Management Strategies
ProjectManager.com is a great tool, but it’s also a library of project management. We have tons of blog posts that speak to every aspect of the field and tutorial videos for a more visual approach.
Watch our resident expert Jennifer Bridges, PMP, as she explains IT management strategies and offers some best practices.
Here’s a screenshot for your reference.
Thanks for watching!
Transcription
Today we’re talking about IT risk management strategies and best practices. So, first of all, why do we care about IT, Information Technology?
Well, today IT or Information Technology is so integrated into everything we do. It touches almost every aspect of our life and our business.
So, with IT comes some unique challenges. So, first of all, the technology just continues to change. So, we have to consider can the hardware, software, apps, and any kind of integrations in between them keep up?
Also finding people who are trained and have the expertise we need for all the changing technologies.
Also finding people with good work ethic and what that means is having been able to show up on time, make commitments, make deadlines and follow up and carry through with what they committed to.
There’s also, in IT, because it touches financial services and a lot of other personal data or company data, we have to make sure that everything we do complies with just ongoing new regulations.
So, when we talk about IT risk management, what we’re talking about is the application of risk management methods to information and technology in order to manage those associated risk.
Basically, we’re assessing the business risk associated with the use of, the ownership, operation or adaption of IT in our organization because if we own certain technologies or we’re running on certain platforms or using them, we have to be, again, in compliance and there are some risks to those.
So, how do we do that?
So, here are a few steps that are common to IT risk management.
First of all, we need to identify the risk that are carried through with the use of our IT.
So, we identify the risk, then we analyze the risk. Is this a big risk? Is it a little risk? It could be a small risk, but have a huge negative impact, or it could be a big risk, but if it happens, the impacts could be minimal, so we have to assess and that analyze that.
Then we evaluate and rank those risk and we respond to the risk and we respond to those through the mitigation strategies.
So, we monitor and review those risk constantly.
So, here’s some strategy. So, the strategy…The thing about using strategies is it provides a structured approach to identify, assess and manage those risk.
Strategies also provide a process that you regularly update and review the assessment based on changes that happen to the project, the environment, the economy, whatever.
And then, so, here are common IT risk management strategies.
So, first of all, you apply safeguards. It’s an avoidance. So, a company may decide, “We want to avoid those risks or these risks at all costs. So, do everything you need to do, put all the strategies in place so we can avoid this.”
The second one is transferring the risk. That’s transference. So, you may be transferring that to another group, another organization, maybe an outside company who can handle that better. So, it may be a less of a risk to whoever it is transferred to.
Also, mitigation is one that where you reduce the impact of that risk. You do everything, you put all the processes, methodologies, teams, whatever in place to mitigate it if it does happen.
And then the fourth one is you accept the risk, you know going in what the risks are, and then you accept it without control or mitigation. You just say, “If this happens, we’re gonna go ahead and accept it, we’re gonna deal with it if it occurs.”
So, here are some best practices that I think are really important.
Number one, evaluate these risks early and often. Sometimes people wait until they’ve encountered a risk before they even think about it. So, before a project ever starts, before any implementation starts or any conversions or migrations or integrations, think through, plan for the risk ahead of time, and then as you go along, again, you’re continuing to assist those.
Also involve the stakeholders because stakeholders may have information that you don’t have that they can bring in, or if you’re discussing, evaluating those they may have other best practices or historical data that will help.
The third one is get sign off. So, whatever strategy that is agreed upon, you wanna be sure that the stakeholder, the owner has sign off in case it does happen – specifically if you agree to accept the risk and it does occur.
So, if you need a tool that can help you with your IT risk management, then sign up for our software now at Projectmanager.com.
(This post was updated December 2019)
No comments:
Post a Comment